When Defender came to macOS as well as Windows, Microsoft announced that the name of the software was changing, from Windows Defender to Microsoft Defender. Hidden in the presentation was a hint about the future: a Linux laptop with a penguin sticker on. Now Microsoft Defender ATP for Linux is in public preview for Red Hat Enterprise Linux 7+, CentOS Linux 7+, Ubuntu 16 LTS or higher, SLES 12+, Debian 9+, and Oracle Enterprise Linux 7. But what does it actually protect those OSes from?
Microsoft already has Linux malware detection in the Defender agents on Windows and Mac, because files get moved from one device to another and you want to catch malware wherever it is — ideally, before it gets onto a vulnerable system. If you’re using WSL, Defender already protects you against threats like infected npm packages that try to install crypto miners.
Mac came first because that’s the order that Microsoft’s enterprise customers asked for, says Rob Lefferts, corporate vice president for Microsoft 365 security. “We’re working to address all of the endpoints that are problematic for our customers, starting with Mac and moving to Linux — particularly Linux on the server, which is the focus right now — and then thinking about iOS and Android and how we protect those mobile endpoints.”
The long-term result, says Lefferts, is comprehensive endpoint security: “That includes next-gen protection, things like antivirus as well as behavioral [protection] in addition to EDR [endpoint detection and remediation]. Everything that we do for Defender, we want to make sure that that works across all the platforms in the places that they are most especially vulnerable.”
For smartphones, Microsoft seems likely to concentrate on phishing, and not just in email but potentially in messaging apps too. “We have a bunch of very broad assets around detecting malicious campaigns and sites, and we’re bringing that to bear to help on mobile,” Lefferts says.
The problem is that when you get better at protecting one area like email, attackers move to other areas (which is why Office 365 ATP now covers SharePoint).
“There are a lot of other channels on a mobile device that is being used for communication and collaboration because it’s a natural place for it. This fits into how we think about security more comprehensively, which starts with all endpoints that you care about,” says Lefferts. “But then let’s move past endpoints — let’s talk about your whole estate, all of your users and all of your data and all of your communication tools inside of one threat protection environment.”
Thinking in graphs
When Defender ATP is generally available for Linux at the end of 2020, that comprehensive endpoint protection will include “a wide range of exactly the same kind of detection tools that you see on Windows,” Lefferts says. “The initial release does not include all of the remediation action capabilities that we have in Windows, but it is something we aspire to add to it over time.”
Antivirus is a tricky term these days, Lefferts notes — he talks instead about “the on-box, protective measures that take action immediately” — because there are so many more threats than viruses, especially scripting and fileless attacks. “We envision that as being part of the offering, but it’s starting much more focused on executable objects.”
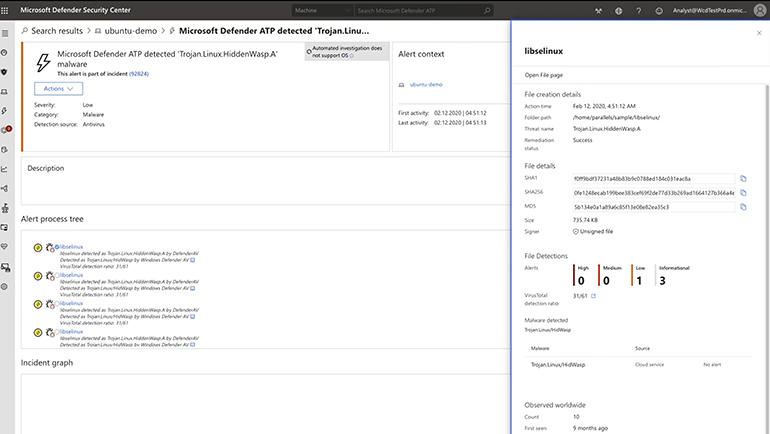
The preview can spot and block malware and ‘potentially unwanted applications’ (PUAs). There isn’t much adware for Linux, but coin miners could be something you install or something you get tricked into installing, and even legitimate remote admin tools are a problem if it’s an attacker putting them on the system. Just as importantly, it sends that information to the Defender Security Center.
Defender is really two things. There’s the agent that runs on the endpoint: scanning files, tracking what happens in the OS, detecting malware on the device and blocking or removing it (as well as giving you the option to control what apps can run, but also sending signals to the Defender Advanced Threat Protection cloud service where information from multiple systems is correlated.
Attackers don’t think about separate devices and systems, or even a list of targets: they think about how systems are connected to each other and how they can move from one infected device to others in the same environment to take control, extract the most data and stop the security team from kicking them out. A laptop with a virus on, a dozen failed password attempts on one server and unusual file access on another aren’t three separate problems: they’re an attacker moving across the network and getting access to more systems.
Defenders need that same kind of graph view of the system, and the more systems that Defender ATP can get signals from, the clearer view you’ll have to attacks. This is the idea behind the Microsoft security graph, which can add events like users clicking a phishing message in Outlook on one of their devices, or a link in a Word document that downloads a macro that in turn downloads a crypto miner. Now Linux systems can feed into that graph, Lefferts explains.
“One of the main reasons for doing this is to connect this protection into your enterprise system. Defender is about end-to-end protection for endpoint devices in your environment — it’s plugged into Defender ATP as an EDR system, the signals are showing up in one consistent dashboard and it’s detecting events and attacks, and providing security teams and SOC analysts with the tools they need to understand that bigger picture,” he says.
“At the end of the day, attackers are after customers’ data in one form or another — whether to delete, encrypt, doxx, steal, whatever. But one of the key objectives along that path is getting persistence on the server backbone environment in the company. It’s a central point from which they can just latch on to everything else and get carried along because end-users always keep coming back to these. Sometimes that’s Active Directory, sometimes that’s just an application server, and from there I can now attack, willy-nilly across end-users in the environment.”
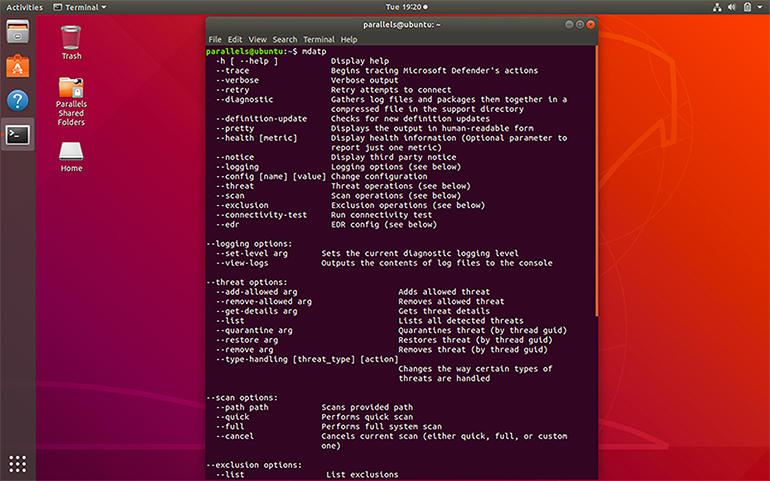
Image: Microsoft
Command-line control
That’s why Defender on Linux is initially focused on servers and DNS, says Lefferts: “Linux machines, entire machines, are being used as platforms for applications”. That includes VMs running in the cloud, and because it’s aimed at servers, Defender doesn’t have a user interface on Linux — it’s all run from the command line, it works with the usual Linux-management tools like Ansible, Chef, and Puppet, and configuration options are in a JSON file. You also need to make sure you have preview features turned on in the Microsoft Defender Security Center to see details from the protected Linux systems.
Keeping security tools up to date is important, but as with WSL distros, Microsoft is avoiding auto-updates in favor of letting Linux users manage their own update schedules for the Defender agent. Companies will likely already have processes in place for that, using scripts, tools like Landscape or the standard unattended-upgrades option. Signatures and threat definitions will be pushed to the Defender agent automatically though (on Windows, that happens several times a day).
There’s nothing to stop you running Defender on a developer laptop running Linux if you want to protect it. “We are not yet targeting Linux as a desktop or user endpoint — again, primarily because of the GUI issue, although it does work. So, if you’re talking about folks like coders, they might be able to survive in that environment but it’s not something that we would turn loose on regular users,” Lefferts warns.
If you’re using Linux as a development platform and building your own custom apps based on open-source projects, those can come with vulnerabilities, and enterprises want monitoring that helps catch those. Development tools might help with this before they’re deployed, but Microsoft Defender already detects open-source tool kits when they’re a threat, and the same will be true on servers. “It’s not just that those bits are present on the disk, it’s that they’re actually getting used and loaded into memory,” says Lefferts.
There are some Linux systems Defender isn’t a good fit for at this stage. “When it comes to the broader ways in which Linux gets used — embedded in IoT devices or phones or all the places it might end up — we are definitely not targeting those scenarios at this point,” Lefferts says. Azure Security Center for IoT is a better option for managing IoT security, for example.
The ability to look across all the end-user endpoints and server infrastructure in your environment will be a step forward for many enterprises. But bringing Defender to Linux is part of the bigger security strategy of moving from detecting attacks to preventing them by hardening the environment — and prioritising problems.
“If defenders are going to be more successful, they really do need to be able to see the landscape in the same way that the attackers do, which is everything chained together in one story,” Lefferts points out. “That includes not only pulling in the servers, but pulling in email and the reuse of identity, and how this connects to the cloud applications, cutting across all those domains into one consistent incident, which is the object that we use to tell that story for defenders.”
“We can use this not just to tell the SecOps team when an attack happens, but also to tell security admins and the broader IT team about where the vulnerabilities of concern lie, with the ability to reorder that dynamically based on the threats in the landscape. This will help the organization understand what are the biggest security posture problems that they need to go fix.”
If you’re not ready for that kind of big picture, Defender for Linux is still useful, Lefferts insists. “If heaven forbid, you aren’t using anything to protect your Linux estate today, you can start immediately with Defender when it’s GA. Or if you’re using a separate tool, you don’t have to do that anymore: you will actually get better protection by deploying something that’s integrated with Defender ATP.”
TechRepublic




